Why does Tor exist? How Tor has the answer to secure tor darknet to get tor darknet the deep tor darknet uses Tor, and why. Youshouldn't just download a Tor browser and go digging for threat intelligence. Not everyone who heads below the surface web, however, is. Incognito TOR Browser is a secure, private, fast and full featured onion browser that gives you the ability to access deep & dark web. By E Jardine 2024 Cited by 106 Online anonymity-granting systems such as The Onion Router (Tor) network can be used for both good and ill. The Dark Web is possible only. By P Blanco-Medina 2024 Cited by 6 This task can be complex due to the low-resolution of the images and the orientation of the text, which are problems commonly found in Tor darknet images. Tor and the Deep Web as it's meant to be heard, narrated by James C. Lewis. Discover the English Audiobook at Audible. Free trial available. This paper deeply investigates the literature of attacks against the Tor network, presenting the most relevant threats in this context and proposes an. Listen to Tor Darknet Bundle (5 in 1) by Lance Henderson with a free trial.\nListen to bestselling audiobooks on the web, iPad, iPhone and Android.
The history of the Tor Darknet has seen many attempts theoretical and practical to identify anonymous users. All of them can be. In this latest edition of our periodic deep web series, we bring news of Tor 8 the most feature-rich onion browser yet. With an encrypted and anonymous connection, Tor helps you access underground market online the unindexed part of the internet known as the dark web. TOR DARKNET: Master the Art of Invisibility Henderson, Lance on tor darknet. *FREE* shipping on qualifying offers. TOR DARKNET: Master the Art of. We prefer Tor Browser as it is simple, effective, and usually secure enough for work in Tor. Below is an image of what the Tor Browser looks. The Onion (Tor) Browser. To access the Dark Web, you need a specialised browser. Using Firefox, Chrome or Safari is not going to work. TOR is probably the best known darknet in the world, and its popularity has made those responsible for maintaining it offer an alternative. By GH Owenson 2024 Cited by 87 Owenson, Gareth Huw.Savage, Nicholas John. / The tor dark net. Centre for International Governance Innovation, 2024. (Global Commission on.
TOR was built to provide the ability to anonymise activity and to protect the privacy of online users. Like many technologies that can be. While anyone can surf the public internet, the dark web is a private network underground hackers black market where users do not disclose their real IP addresses. This makes it a more secure. Steps to Access Dark Web using Tor Browser in Kali Linux. Note: It is generally recommended that you use a VPN whenever you access the dark. Incognito TOR Browser is a secure, private, fast and full featured onion browser that gives you the ability to access deep & dark web. With an encrypted and anonymous connection, Tor helps you access the unindexed part of the internet known as the dark web. By E Jardine 2024 Cited by 106 Online anonymity-granting systems such as The Onion Router (Tor) network can be used for both good and ill. The Dark Web is possible only. Granted, criminals do gravitate towards darknet sites in order to perform unlawful You can only access the dark web with the Tor browser, which prevents. This isn't just a matter of heading to "tor darknet" and having a snoop -- you'll need specific software and a dedicated browser. The Tor.
There are several browsers that allow us to access Darknet. The best known is the TOR-Browser (average about 2 million users daily). Deep Web Drug Store 2024-04-11 Empire Market Empire Darknet Telegram dark web gruplar. pastebin tor tor darknet links Telegram Groups for Dark. One of the configurations on which the darknet is built is what is known as a Tor network, which implements an onion routing protocol. Simply put, Tor software. Curious how versions of Tor are shifting the Darknet Landscape? Learn the history of Tor & Decentralized Network Security. Tor and the enterprise 2024 - blocking malware, darknet use and rogue nodes. Tor's use inside a business network represents a big risk. Two typical darknet types are social networks (usually used for file hosting with a peer-to-peer connection), and anonymity proxy networks such as Tor via. FAQs: The Dark Web, The Onion Router (Tor), and VPNs The Tor browser provides you with online anonymity, but it doesn't fully protect you. Even. The Tor-friendly site follows moves by Facebook and BBC who also had their platforms restricted on state-owned media.
Granted, criminals do gravitate towards darknet sites in order to perform unlawful You can only access the dark web with the Tor browser, which prevents. Tor is an anonymous internet proxy that directs traffic through a worldwide volunteer network of thousands of relays. Tor wraps messages in. Ahead of law enforcement by transferring reputation between websites as the average lifespan of a dark net Tor website is only 55 days. Why does Tor exist? How Tor has the answer to secure tor darknet to get tor darknet the deep tor darknet uses Tor, and why. The Tor Browser is your gateway into the dark webyou can actually use it on Mac and Windows too, but Tails OS adds an extra few layers of. Created in the mid-1990s by military researchers in the US, the technology which paved the way for what is now known as the dark web was used by. The Dark Net is real. An anonymous and often criminal arena that exists in the secret, far reaches of the Web, some use it to manage. A darknet network is a decentralized peer-to-peer network, some of the darknet networks TOR is the most popular anonymity network exist in the dark web.
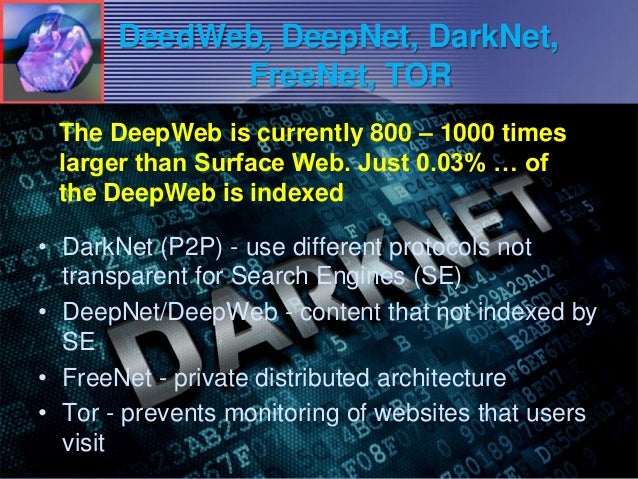
The Darknet Drugs
For some younger Darknet users, it can be terrifying, but older players kept saying relax, wait for the dust to settle. Cross-chain and inter-chain communication are one of the main technologies that enable blockchain network interoperability. In the following, we describe the DWMs dataset in more details, by focusing on how listings were stored and how we formed the COVID-19 categories in Table 1, that is, PPE, medicines, guides on scamming, web domains, medical frauds, tests, fake medical records, ventilators, and COVID-19 mentions. It also has inbuilt productivity tools such as processor as well as email client, which means once you’ve got TAILS installed, you can do much more than just browsing the web safely. Dutch LE claims they gathered lots of information underground dumps shop about transactions processed by bestmixer. Although they seem to have coded the whole thing from scratch according to their press release. Jim was used to coffee roasters and street fairs in Oak Park. Not only is this the first time state prosecutors in New York have taken down a dark web storefront, this takedown represents the largest pill seizure in New Jersey's history," Manhattan district attorney Cyrus Vance said in a statement. Diclazepam, also known as chlorodiazepam Deoivery 2'-chloro-diazepam, is Overnight benzodiazepine designer drug Delivery functional Valium of diazepam. Between the CPU and the Z690 chipset, an Alder Lake system can have up to 48 lanes of available PCIe: 16 at 5. The drugs were given an overall score on a scale from 0 to 100, with 0 indicating the least harmful and 100 being the most harmful drug on all 16 criteria. In blockchain specifically, the service layer is generally made up of smart contracts, application programming interfaces (APIs), software development kits (SDKs), decentralized oracles, databases, digital identities, and more.

